Table of Contents
A. macOS Open Directory (GUI)
B. Windows Active Directory (GUI)
Appendix I - Setup Windows Active Directory with IDMU (Identity Management for UNIX)
Appendix II - Add the IDMU role to Windows Server (Example illustrated with Windows Server 2008)
Appendix III - Add UNIX Attributes to AD | User and Group
C. Linux Open LDAP with PDC
D. Samba Login Tool Instructions (Only applicable to macOS Open Directory)
E. Adding Permissions to the NAS Gateway SMB Share
Scope
The purpose of this article is to provide an A-Class SAN administrator the appropriate instructions on binding their
A-Class and NASGW to an External LDAP server.
Internal and External LDAP servers cannot be enabled at same time. There are three LDAP statuses:
- Internal LDAP enabled while External LDAP is disabled
- Internal LDAP disabled while External LDAP is enabled
- Internal and External LDAP servers are both disabled
There are (3) types of External LDAP servers that are supported:
- Windows Active Directory
- macOS Open Directory or Linux LDAP without PDC
- Linux LDAP with PDC
Select “Enable External LDAP Server” to enable the external LDAP module. If the Internal LDAP module is enabled, it will be disabled when the External LDAP is selected.
Setting Description
The table below demonstrates the external LDAP settings in the A-Class GUI.
Note: Some of the settings are common for all the supported LDAP servers; however, certain settings may not be supported on some of the LDAP servers. For more information, please contact Technical Support.
|
Setting Item |
Description |
|
SSL |
Possible value: True or False. It should be set to False if LDAP server doesn’t support SSL. |
|
Timeout |
Timeout value in second. Value is from 1 to 30 seconds. Default is 10 seconds |
|
BaseDN |
The BaseDN of LDAP server. If the server is ptu.promise.com, the value shall be “dc=ptu,dc=promise,dc=com”. Note that there shouldn’t have space character in the value. |
|
Server |
The IP address of LDAP server. |
|
Port |
The port of LDAP server. Default value is 389 |
|
SAMBANetBIOSName |
NetBIOS name for Samba server running in NAS Gateway. Optional value if there isn’t NAS gateway configured. |
|
ServerType |
LDAP server type. Three types are supported: Windows AD, Mac OD and Linux OpenLDAP. |
|
Samba NetBIOS |
This setting is enabled for “Linux LDAP with PDC” only. |
|
AnonymousBind |
Possible values: True or False. True: Bind LDAP server by using anonymous. LDAP server must support it. False: Don’t use anonymous user to bind LDAP server. BindDN (username) and BindPassword must be provided. |
|
BindDN |
Bind username When Windows AD is set up, four types of BindDN can be used: 1. <Domain_Name>\<Username> Such as: example.com\Administrator 2. <Username>@<Domain_Name> Such as: Administrator@example.com 3. CN=<Username>,CN=users,DC=<Domain_name> For example:
Note: “users” must be lower case. “Users” doesn’t work for NAS gateway
If Windows AD is on Windows 2000 or earlier version, type #1 is suggested. For other versions, all 3 types can be used.
Note: <Username> only doesn’t work for NAS gateway. NAS gateway will report “LDAP connection failed” if type in username only.
|
|
BindPassword |
Bind password. The password of the username which is used in BindDN |
|
UIDAttribute |
Attribute containing the LDAP username. Default values for different LDAP servers: - Mac OD: uid - Windows AD: uid (Identity Management for UNIX must be installed and UNIX Attributes must be configured) - Linux OpenLDAP: uid Other possible values can be checked on different LDAP server setup: - Windows AD: sAMAccountName, cn |
|
ObjectClass |
The object class to get user entries from LDAP server. The below hierarchy of object classes, the value can be user, organizationalPerson or person. Value cannot be top, because top is the root class and cannot be used to filter user. objectClass: top
Default values for different LDAP servers: - macOS OD: posixAccount - Windows AD: user - Linux OpenLDAP: posixAccount |
|
GroupIDAttribute |
Attribute containing the LDAP group name. Default values for different LDAP servers: - Mac OD: cn - Windows AD: cn - Linux OpenLDAP: cn Other possible values can be checked on different LDAP server setup: - Windows AD: sAMAccountName |
|
ObjectClass ofGroup |
The object class to get group entries from the LDAP server. The below hierarchy of object classes, the value can be group. Value cannot be top, because top is the root of the class hierarchy and cannot be used to filter group. objectClass: top objectClass: group
Default values for different LDAP servers: - macOS OD: posixGroup - Windows AD: group - Linux OpenLDAP: posixGroup |
|
EmailNotification forEvent |
True: enable email notification for event. New event will be sent to the email address provided by EmailAddrAttribute. False: disable |
|
FullNameAttribute |
The LDAP attribute to get the full name of email recipient. |
|
EmailAddrAttribute |
The LDAP attribute to get the email address for email notification. With this setting, new events will be sent to the email address automatically. |
|
Privilege for LDAP Users |
Default: Use default privilege selected from next item. Role Mapping: Map LDAP role to subsystem privilege |
|
DefaultPrivilege |
The default privilege for all LDAP users. Used only when previous setting is select to Default. |
A. macOS Open Directory (GUI)
Note: The Samba Login Tool is required. If you don't authenticate your users, the OD users will not be able to login to the SMB shares on the NAS Gateway.
CLI Output
administrator@cli> ldap -v-------------------------------------------------------------------------------
ExternalLDAP: Enabled
SSL: Disabled Timeout: 10 seconds
BaseDN: dc=macserver,dc=promise,dc=com
Server: 192.168.252.159 Port: 389
SAMBANetBIOSName: promise
ServerType: MAC Open Directory or Linux LDAP without PDC
AnonymousBind: Disabled
BindDN: uid=test,cn=users,dc=macserver,dc=promise,dc=com
BindPassword: ******
UIDAttribute: uid
ObjectClass: posixAccount
GroupIDAttribute: cn
ObjectClassOfGroup: posixGroup
EmailNotificationForEvent: Enabled
FullNameAttribute: displayName
EmailAddrAttribute: mail
RolePolicy: default DefaultPrivilege: View
-------------------------------------------------------------------------------
B. Windows Active Directory (GUI)
Please make sure that the AD bind account is part of the Domain Admins group or has sufficient privileges to join the Domain. If you use a standard user (with no Domain Admin Privileges), the LDAP connection will fail.
CLI Output
administrator@cli> ldap -v-------------------------------------------------------------------------------
ExternalLDAP: Enabled
SSL: Disabled Timeout: 10 seconds
BaseDN:dc=ptb,dc=local
Server:192.168.252.111 Port: 389
ServerType: Windows Active Directory
DNS: 192.168.252.111
AnonymousBind: Disabled
BindDN: ptb\test
BindPassword: ******
UIDAttribute: uid
ObjectClass: user
GroupIDAttribute: cn
ObjectClassOfGroup: group
EmailNotificationForEvent: Enabled
FullNameAttribute: displayName
EmailAddrAttribute: mail
RolePolicy: default DefaultPrivilege: View
-------------------------------------------------------------------------------
Appendix I - Setup Windows Active Directory with IDMU (Identity Management for UNIX)
Windows Active Directory is heavily dependent upon DNS. If a DNS IP address has been established in the A-Class, it is recommended that an administrator configures the DNS server to support AD.
If the A-Class is configured with a Linux DNS server, the administrator should create a DNS zone on the DNS server for the AD domain.
If the A-Class is configured with a Windows DNS server, the administrator can configure AD in following (3) ways:
- Install AD on the DNS server; AD and DNS are on the same server.
- Install AD without DNS settings on another server, and use the primary DNS.
- Install AD with DNS settings on another machine, create a DNS zone on the DNS server for the AD domain.
In order to store UNIX attributes in Active Directory, you must install Active Directory and then add the “Identity Management for UNIX” role service (this can be downloaded in Server Manager). Once the role service has been installed, the AD schema now includes a partially RFC 2307-compliant set of UNIX attributes. A new tab labeled “UNIX Attributes” will appear in the properties dialog box for users and groups in Active Directory. Each Active Directory account that will authenticate via Linux must be configured in the new “UNIX Attributes” tab.
Appendix II - Add the IDMU role to Windows Server (Example illustrated with Windows Server 2008)

Appendix III - Add UNIX Attributes to AD | User and Group
If you don't execute this step, the AD users and groups won't populate in the Folder Share setting when applying permissions for the NAS Gateway SMB share(s).
Note: The Samba Login Tool is not required when using Active Directory for authentication.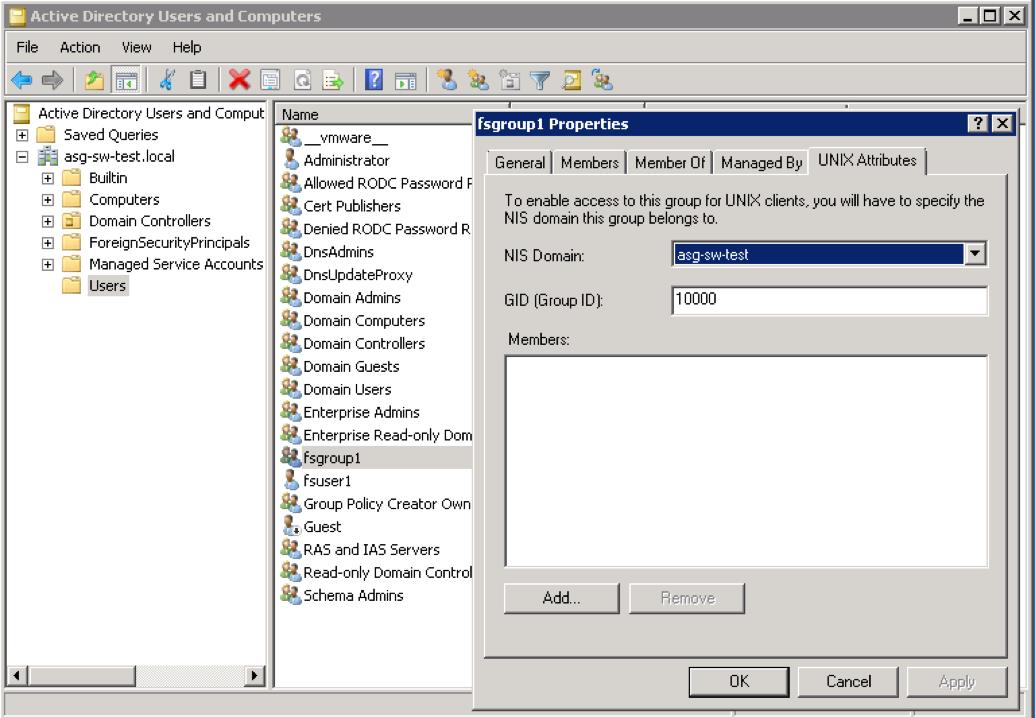

> Install IDMU for Windows Server 2008/2012
C. Linux Open LDAP with PDC
CLI Output
administrator@cli> ldap -v-------------------------------------------------------------------------------
ExternalLDAP: Enabled
SSL: Disabled Timeout: 10 seconds
BaseDN: dc=test,dc=com
Server: 192.168.252.143 Port: 389
SAMBANetBIOSName: test
ServerType: Linux LDAP with PDC
AnonymousBind: Disabled
BindDN: cn=lily,dc=test,dc=com
BindPassword: ******
UIDAttribute: uid
ObjectClass: posixAccount
GroupIDAttribute: cn
ObjectClassOfGroup: posixGroup
EmailNotificationForEvent: Enabled
FullNameAttribute: displayName
EmailAddrAttribute: mail
RolePolicy: default DefaultPrivilege: View
-------------------------------------------------------------------------------
D. Samba Login Tool Instructions (Only applicable to macOS Open Directory)
- Using your web browser, enter the Virtual IP Address of the NAS Gateway Cluster to access the Promise NAS Gateway Samba Login Tool.
- You can retrieve the Virtual IP Address of the cluster by going to NAS Gateway > Detail.

- Enter the user's credentials that you will be authenticating and Login:
If you don’t execute this step, your Open Directory users will not be able to access the SMB share.
- You will receive a message stating that the user has been successfully authenticated.

E. Adding Permissions to the NAS Gateway SMB Share
- Go to NAS Gateway > Mount Point.
- Click the gear and select Folder Share:

- You can set permissions by User or Group.
A. User = Read-Write Example:
B. Group = Read-Write Permission Example
- Click Submit to save the changes and you will receive the following notification message:

Related Articles:
Disable SMB Signing on OS X (10.11.5 > 10.12.x)
Unable to Save File on the NASGW from a File Created by a FC Client - Internal/External LDAP Configurations
VTrak G-Class NAS Gateway Firmware Release Notes
Contact Promise Technology Support
Need more help? Save time by starting your support request online and a technical support agent will be assigned to your case.
Promise Technology Technical Support >

